I am working on a project to both clean up vulnerability technical debt and build a framework for our team to use when prioritising vulnerability remediation going forward.
To that end I am trying to build queries for remdiation projects that have what I believe are the essential criteria for determining risk/ prioritisation, however, I have found that the query builder just doesn’t seem to have all the right compoenents available for selection.
I would like to use the CVSS3 fields to do this but they are not available (as far as I can see). I had thought that perhaps, categories would cover it but I found that not to be the case.
As an example, I would like to set the below crietria as the highest priroty for remediation, but, attack vector and complexity are not available. I had tried using the category network and exploit rank of Novice but the result doesn’t seem to line up.
Attack Vector: Network
Attack Complexity: Low
Remote Code Execution: Yes
Publicly Exploited: Yes
MS Patch: No
Is this the right way to approach this or is there a better way? Perhaps I should just rate them based on the risk score (currently set at real risk). I would apprciate any thoughts or suggestions as to what foks in the community do.
Thanks,
Jamesy
I know its a little convoluted but some of the fields you’re looking for exist at the console level instead of the cloud level. Your best bet would be to create dynamic tags based on the criteria you mentioned and then use those tags in the query builder.
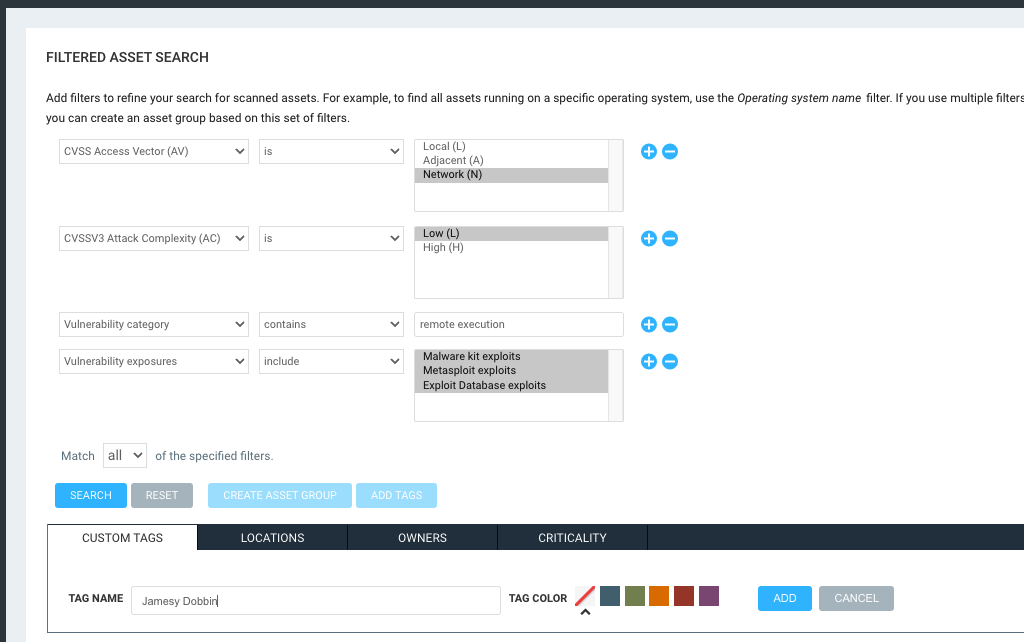
The only thing I can’t seem to find would be the MS Patch. I see nothing that we have outside of SQL that allows you to filter on the available solutions.
I hope this helps!
1 Like
Thanks Josh,
Great shout on these filter options. They are just what I needed.
I would be keen to know how others prioritise remediation. I don’t want to re-invent the wheel, if there is a built in option within IVM that others would use in general I would be open to suggestions.
Jamesy
Generally speaking most customers that I work with simply prioritize based on risk. So using the Real Risk strategy in combination with the Risk Score Adjustment by adding the criticality tags to them. However I’ve seen a wide variety of the filters that customers use to define those tags. Typically speaking though, Domain controllers and public facing assets are always labeled as “Very High” criticality. Additionally it may be beneficial to do the queries like you were suggesting and apply those to criticality tags for Very High.
