Hi all,
I was wanting to create workflows that are triggered from MS teams messages that automate hunting for an IOC.
The process would be analyst issues a command - e.g. !hunt 8.8.8.8 and then the workflow will query different logs inside r7 and other tools (e.g. cortex edr) and return summarised results.
Example being an external IP is found to be of interest, we can add to community threat \ detection rule to know about any future activity but then will want to hunt back and find hosts that interreacted with that IP. Log sources would include firewall, DNS lookups that resolved to that IP, web proxy logs etc etc.
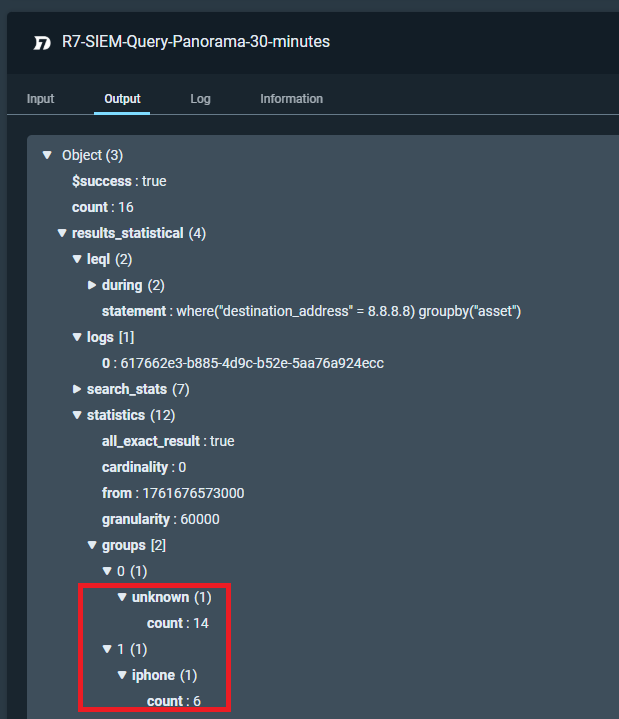
I’ve got a workflow triggering on a ms teams message, it does a LEQL to r7 successfully but im struggling on how to present the information back in a table or otherwise easy to read format.
An example query against the firewall logs looks like: where(“destination_address” = {{[“IP Loop”].[$item]}}) groupby(“asset”)
The loop is if there are multiple IPs added to the trigger it loops through all of them.
E.g. !hunt-ioc 8.8.8.8 1.1.1.1
I can see the output from the query the results live under statistics - groups but im not sure how to extract this. I’ve tried some ai suggestions looping through it with the “jq” plugin but i’m quite lacking in json knowledge.
I’ve had a hunt through the workflows at extensions.r7 and cant see anything there I could adapt. Is anyone able to point me in the right direction please ? Open to any solution.
Thanks in advance!